
Multiple tools allow the creation of infrastructure as code. AWS has its tool, CloudFormation, being very useful and working natively with the rest of AWS services. However, many engineers find that customers look for solutions that can be adapted to other providers without AWS services in their daily work. For this reason, AWS allows integration with platforms such as HashiCorp Terraform. Terraform is an open-source tool for creating, changing, and versioning infrastructure safely and efficiently. AWS with Terraform can be managed similarly to CloudFormation.
In this article, Terraform will generate the infrastructure and implement it automatically through CI/CD. Infrastructure state files must be preserved for later reference, modification, or destruction by subsequent deployments to a durable backend. The CI/CD solution is flexible enough to implement many other AWS services.
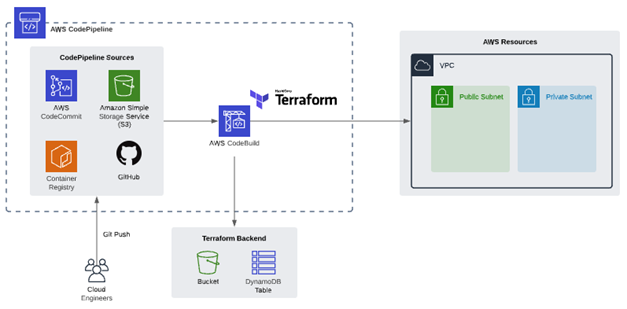
For this solution, we will use AWS CodePipeline, an automated service to form the foundation of the CI/CD pipeline. CodePipeline helps us automate our release pipeline through build, test, and deployment.
We will use AWS CodeBuild, a fully managed CI service that compiles source code, runs tests, and produces software packages that are ready to deploy.
First, generate the infrastructure that will serve as a Backend for AWS and Terraform. A new Amazon Simple Storage Service (S3) bucket and Amazon DynamoDB table store the Terraform state files outside the CI/CD pipeline. Terraform uses these files to map the resources to the configuration, keep track of metadata, and improve performance for large infrastructures.
CodeCommit will be used as a repository, as it offers data security, and it can be integrated with AWS IAM to provide detailed access to information. Within this repository, you will find the configuration files for Terraform and the files for creating the infrastructure.
We must create file to initialize the Master branch that will not interfere with the build process. It can be a txt or informational file, and since it is not important to the process, it can be deleted later.
Create a Terraform file, which contains the following code:
The infrastructure provider to use is specified in our case is AWS, and then the Backend code used by Terraform is generated. Once these two blocks have been created, we proceed to build the infrastructure in AWS, for example, the creation of a VPC with two Subnets.
Once this file is configured, we will save it with the name "main.tf".
Now we must create the file "buildspec.yaml" which will deploy Terraform within CodeDeploy and execute the Terraform plans.
It is important to obtain the most recent version of Terraform, to ensure that we run the application with the latest updates.
For the pre_build section, the Terraform init command will be placed, which is responsible for initializing the Terraform components.
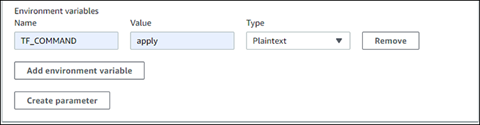
Then in the build section, the command "Terraform $ TF_COMMAND -auto-approve" will be included, which will generate a self-approval instruction for applying the changes in the Terraform template.
And finally, the command "echo Terraform $ TF_COMMAND completed on` date` " is appended in the post_build section, which is simply a message that informs us about the date on which this deployment was completed.
Using Git Bash we will upload these files to our repository in AWS CloudCommit. It can be loaded directly to the main / master branch or some other secondary branch and then merged with the main / master branch, depending on the CI/CD policy that you want to implement.
Next, the release flow will be created with AWS CodePipeline. The data origin will be taken from AWS CloudCommit.
After launching the pipeline, a status view will show, whether the execution was carried out incorrectly or completed successfully. In the same way, we can enter the CodeBuild to have a more detailed view of what is happening within the execution, this only by selecting the Build option in the pipeline.
We can also see previous CodePipeline runs by choosing the History view on the navigation pane on the left. This view is also helpful for viewing multiple concurrent CodePipeline executions.
The pipeline will fail in the first creation attempt due to the user's lack of permissions, so if this error occurs, it is necessary to assign the required permissions for this deployment.
Once the pipeline is executed, it generates an error because the role cannot create the resources and access to S3 and the Dynamo table. Therefore it is necessary to modify the role used by CloudBuild.
Having completed the steps above, we can now relaunch the pipeline.
In this article, we learned how to use AWS Developer Tools to create a CI/CD pipeline that we can use to automate AWS Terraform deployments of infrastructure. By using Terraform and CI/CD, the engineers can: